https://twitter.com/MGMResortsIntl
From what I can understand from various sources (facebook, twitter, news)
* Some methods of checkout is down (but apparently tv checkout was working)
* Credit card payments at restaurants are down (not clear if all or some locations)
* Slot machines can't print tickets
* Slot machines are down
If this is as bad as it sounds, it will be interesting how much this ends up costing MGM AND how long it takes for them to get back up to speed.
As a comparison, my personal website and family email) was hosted by a small-medium sized host. They recently got hit by a ransomware attack and this effectively killed the company. All backups and EVERYTHING was lost. They barely even knew who their customers was and had no way to recover.
https://twitter.com/iamofdaniel/status/1701277365295292512
Has something like this ever happened before on this large a scale? I suppose someone at MGM is happy this happened Monday morning and not Friday night.
Quote: MukkeAll slots at Aria apparently down. No printing tickets for existing balances
https://twitter.com/iamofdaniel/status/1701277365295292512
Has something like this ever happened before on this large a scale? I suppose someone at MGM is happy this happened Monday morning and not Friday night.
link to original post
I kept quiet but back in May on a Friday evening this happened at Borgata.
I lost nearly 100 players cards because the pin information became lost. I had to pay my people to go fix them.
This is one month prior to the Borgata doing a separate crackdown at E-Baccarat tables so I basically had my operation there go down so don't mind discussing it here now.
I suspect now that Borgata incident was a test run. Of course it may be unrelated. Hotels were not affected as I was staying that weekend at borgata. My hotel keys were fine.
But vouchers uncashable at slots was across the property. Everyone had to be cashed out manually. Freeplay became unavailable. And the end result was once they got the system running again any card I used that day the pin was toast
Quote: @LasVegasLocallyThe hackers who took down MGM Resorts' computer networks are asking for a large ransom, according to an insider.
Take it with as big a grain of salt as you wish.
Quote: MukkeAll slots at Aria apparently down. No printing tickets for existing balances
https://twitter.com/iamofdaniel/status/1701277365295292512
Has something like this ever happened before on this large a scale? I suppose someone at MGM is happy this happened Monday morning and not Friday night.
link to original post
Wasn't it Luxor where the slot floor went down about two years ago and people couldn't cash out for over 24 hours?
MGM is currently under a terrorist cyber attack.
Coincidence???
Quote: darkozToday is of course September 11th.
MGM is currently under a terrorist cyber attack.
Coincidence???
link to original post
It started yesterday morning.
The data backup has to be isolated from the active servers to keep it safe from hackers. It could take a while to understand the attack vector and then secure the active servers before they can even start to restore them using backup data. The MGM casino is apparently a victim of sophisticated criminals. None of this is easy, and rushing recovery can make the situation worse.Quote: rxwineCasinoís canít afford proper backup? Ransomware attacks have only been occurring and warned about for years now. Sorry, not sorry.
link to original post
Don't understand how ransomware could affect backups to the point of killing the company?Quote: MukkeAs a comparison, my personal website and family email) was hosted by a small-medium sized host. They recently got hit by a ransomware attack and this effectively killed the company.
All backups and EVERYTHING was lost. They barely even knew who their customers was and had no way to recover.
link to original post
When i was in charge of backups, I did Father-Son-Grandfather backup scheme.
The weekly backups was locked up on site and monthly backups were stored off site.
I probably should have been more secure about the daily backups.
I agree that it should not be possible to lose all the backups. But IT is run by humans, and humans are fallible. I'm sure everytime something like this happens, it departments take a moment to consider how and why, and what they can do to double check they wouldn't be susceptible to the same.
> When i was in charge of backups, I did Father-Son-Grandfather backup scheme.
> The weekly backups was locked up on site and monthly backups were stored off site.
Was this recently or today? In the old days, this was "simpler" because tape backups lend itself well to physical removal from the network. Today I don't think companies rely on tape backups (too slow), so the physical separation requires more deliberation. Sure, you can have logical separation of network - but again - logical separation is only a configuration change away from no longer being separated - i.e. human errors or even hacks can have profound impact.
yes tape backup and waaaay before cheap terabyte ssd'sQuote: Mukke> When i was in charge of backups, I did Father-Son-Grandfather backup scheme.
> The weekly backups was locked up on site and monthly backups were stored off site.
Was this recently or today? In the old days, this was "simpler" because tape backups lend itself well to physical removal from the network. Today I don't think companies rely on tape backups (too slow), so the physical separation requires more deliberation. Sure, you can have logical separation of network - but again - logical separation is only a configuration change away from no longer being separated - i.e. human errors or even hacks can have profound impact.
link to original post
this hacking is one reason why a slot mgr can't change slot machine payback from his desk.Quote: MrVhttps://www.youtube.com/watch?v=P19XrDJL-5k
link to original post
Still requires physical access (ie: key) to get into the slot to change parameters
I would imagine that's the case but have yet to see it mentioned
Quote: darkozSo does anyone know if patrons are unable to access their freeplay offers? Are pin numbers no good at kiosks?
I would imagine that's the case but have yet to see it mentioned
link to original post
A friend couldn't do freeplay yesterday or today at National Harbor. I didn't ask if his pin number worked at the kiosks.
Slots working now? TiTo fixed? You can cash out using the ATM machines?Quote: ChesterDogQuote: darkozSo does anyone know if patrons are unable to access their freeplay offers? Are pin numbers no good at kiosks?
I would imagine that's the case but have yet to see it mentioned
link to original post
A friend couldn't do freeplay yesterday or today at National Harbor. I didn't ask if his pin number worked at the kiosks.
link to original post
Just player cards not working?
Quote: darkozSo does anyone know if patrons are unable to access their freeplay offers? Are pin numbers no good at kiosks?
I would imagine that's the case but have yet to see it mentioned
link to original post
For Borgata: unable to access Kiosk at all. At slot machines, slot dollars showed up, but Freeplay did not show.
Quote: 100xOddsSlots working now? TiTo fixed? You can cash out using the ATM machines?Quote: ChesterDogQuote: darkozSo does anyone know if patrons are unable to access their freeplay offers? Are pin numbers no good at kiosks?
I would imagine that's the case but have yet to see it mentioned
link to original post
A friend couldn't do freeplay yesterday or today at National Harbor. I didn't ask if his pin number worked at the kiosks.
link to original post
Just player cards not working?
link to original post
My friend is only interested in the freeplay. I didn't ask if the TiTo and the cash redemption machines were working.
Here's a YouTube of a Fox 5 report that mentions that at 6:30 AM Tuesday the machines and tables seemed to be operational.
ALPHV ransomware group compromised MGM Resorts by hopping on LinkedIn, find an employee, then call the Help Desk.
1. Look up who works at a org on LinkedIn
2. Call Help Desk (spoof phone number of person Iím impersonating)
3. Tell Help Desk I lost access to work account & help me get back in
10min conversation brought down a multi-billion $ company.
It sounds like some machines work some down. Some TITO works and some don't.
It sounds like player tracking for earning points IS working, but accessing your account for freeplay etc is not.
It sounds like some places you CANNOT charge to room, while other players PREFER you charge to room. Obviously not being able to charge to room will have a big effect on being able to take advantage of comps.
I just bought a lottery ticket some puts. It seems only appropriate to gamble in a situation like this. :)
Could not use comps at any restaurants.
So I am assuming they expect to not be fixed before the 17th
Two sources familiar with the matter told Reuters the hacking group Scattered Spider was behind it. Identified by analysts last year, this group uses social engineering to lure users into giving up their login credentials or one-time-password (OTP) codes to bypass multi-factor authentication, the security firm Crowdstrike said in a blog post in January.
It is "one of the most prevalent and aggressive threat actors impacting organizations in the United States today," Charles Carmakal, chief technology officer at Alphabet Inc's (GOOGL.O) Mandiant Intelligence said in a post on LinkedIn on Wednesday, following reports about the MGM breach.
Quote: ams288Quote: darkozToday is of course September 11th.
MGM is currently under a terrorist cyber attack.
Coincidence???
link to original post
It started yesterday morning.
link to original post
Did it start Sunday morning or Sunday evening?
If it was in the evening the reason for the "September 10th" attack could have been a time zone shift. They are saying this came from Russia.
The other possibility is the ransom was delivered before 9-11 and MGM shut down their system before the actual deadline.
It just seems too coincidental to not be a 9-11 chosen event.
Quote: 100xOddsRumor:
ALPHV ransomware group compromised MGM Resorts by hopping on LinkedIn, find an employee, then call the Help Desk.
1. Look up who works at a org on LinkedIn
2. Call Help Desk (spoof phone number of person Iím impersonating)
3. Tell Help Desk I lost access to work account & help me get back in
10min conversation brought down a multi-billion $ company.
link to original post
https://cybernews.com/security/mgm-cyberattack-claimed-alphv-blackcat-ransomware-group/
If it's true that Caesars coughed up a $30m ransom, then their management want their arses kicking. Pay these extortionists their ransom only emboldens them and pays their IT costs for the next attack.
Quote: darkozQuote: ams288Quote: darkozToday is of course September 11th.
MGM is currently under a terrorist cyber attack.
Coincidence???
link to original post
It started yesterday morning.
link to original post
Did it start Sunday morning or Sunday evening?
If it was in the evening the reason for the "September 10th" attack could have been a time zone shift. They are saying this came from Russia.
The other possibility is the ransom was delivered before 9-11 and MGM shut down their system before the actual deadline.
It just seems too coincidental to not be a 9-11 chosen event.
link to original post
Maybe it is likely they even infiltrated the system earlier but intentionally sprung it on the appropriate day. Of course, misleading investigators is good for illegal business. Making it look like a different group did it may have fooled no one though. They always seem to know the general area that the attack came from. Or at least, seems so.
Quote: OnceDearQuote: 100xOddsRumor:
ALPHV ransomware group compromised MGM Resorts by hopping on LinkedIn, find an employee, then call the Help Desk.
1. Look up who works at a org on LinkedIn
2. Call Help Desk (spoof phone number of person Iím impersonating)
3. Tell Help Desk I lost access to work account & help me get back in
10min conversation brought down a multi-billion $ company.
link to original post
https://cybernews.com/security/mgm-cyberattack-claimed-alphv-blackcat-ransomware-group/
If it's true that Caesars coughed up a $30m ransom, then their management want their arses kicking. Pay these extortionists their ransom only emboldens them and pays their IT costs for the next attack.
link to original post
I donít know, when itís all said and done, I suspect MGM is going to wish they could have just paid $30 mil to avoid this mess.
I bet they will. Somebody somewhere is hiring a lawyer.Quote: ams288Quote: OnceDear
https://cybernews.com/security/mgm-cyberattack-claimed-alphv-blackcat-ransomware-group/
If it's true that Caesars coughed up a $30m ransom, then their management want their arses kicking. Pay these extortionists their ransom only emboldens them and pays their IT costs for the next attack.
link to original post
I donít know, when itís all said and done, I suspect MGM is going to wish they could have just paid $30 mil to avoid this mess.
link to original post
Seems like it shouldn't be that hard to assign a security pass that can't be easily transferred. Everyone uses a two-part authentication where one is a physical on-site key.
Say someone impersonating the big boss calls in and gets an employee to release partial info? The big boss should still have to enter a special code from home on his phone or computer to use the on-site access. The employee can only do half; the person impersonating the boss on the other end has to have the right personal info as well.
Quote: rxwineI forget who was one of the infamous early hackers, but I remember reading that he got much of his inside hacks from the weak human factor. Tricking someone, in other words for a password.
link to original post
At my previous employer, there was a spear-phishing incident that came damned close. The Finance director received an email from the CEO instructing her to pay an urgent invoice of several thousand pounds immediately. The email featured a well formed invoice as an attachment along with target bank account details. She got as far as logging into the online bank before remembering that she was due to see him that very morning for a meeting. So she waited till that meeting to confirm final payment. It was all very believable and very slick. Our senior managers were/are our biggest vulnerability. They insisted on having full admin rights to their laptops and all systems and were complete mavericks with their passwords. The Chairman of the company kept all of his passwords in a diary in his laptop bag in plain text. He carried sensitive documents on his USB stick and got angry with IT when it was suggested that he encrypt it. A hackers paradise.
Quote: rxwineI forget who was one of the infamous early hackers, but I remember reading that he got much of his inside hacks from the weak human factor. Tricking someone, in other words for a password.
Seems like it shouldn't be that hard to assign a security pass that can't be easily transferred. Everyone uses a two-part authentication where one is a physical on-site key.
Say someone impersonating the big boss calls in and gets an employee to release partial info? The big boss should still have to enter a special code from home on his phone or computer to use the on-site access. The employee can only do half; the person impersonating the boss on the other end has to have the right personal info as well.
link to original post
If they fooled the employee they can fool the supervisor as well.
Fingerprint analysis while it can still be faked would mean a physical finger for entry would be needed. At least getting into an IT infrastructure would require login at the source computer. Not remotely like here.
Quote: OnceDearQuote: rxwineI forget who was one of the infamous early hackers, but I remember reading that he got much of his inside hacks from the weak human factor. Tricking someone, in other words for a password.
link to original post
At my previous employer, there was a spear-phishing incident that came damned close. The Finance director received an email from the CEO instructing her to pay an urgent invoice of several thousand pounds immediately. The email featured a well formed invoice as an attachment along with target bank account details. She got as far as logging into the online bank before remembering that she was due to see him that very morning for a meeting. So she waited till that meeting to confirm final payment. It was all very believable and very slick. Our senior managers were/are our biggest vulnerability. They insisted on having full admin rights to their laptops and all systems and were complete mavericks with their passwords. The Chairman of the company kept all of his passwords in a diary in his laptop bag in plain text. He carried sensitive documents on his USB stick and got angry with IT when it was suggested that he encrypt it. A hackers paradise.
link to original post
My company makes us do at least one yearly training class teaching us how to avoid this exact scenario.
And the security team sends out fake phishing emails occasionally to try to catch us off guard. We have to report the email as a phishing attempt. God forbid if you click the link or open the attachment - then you have to attend another special training.
Quote: ams288Quote: OnceDearQuote: 100xOddsRumor:
ALPHV ransomware group compromised MGM Resorts by hopping on LinkedIn, find an employee, then call the Help Desk.
1. Look up who works at a org on LinkedIn
2. Call Help Desk (spoof phone number of person Iím impersonating)
3. Tell Help Desk I lost access to work account & help me get back in
10min conversation brought down a multi-billion $ company.
link to original post
https://cybernews.com/security/mgm-cyberattack-claimed-alphv-blackcat-ransomware-group/
If it's true that Caesars coughed up a $30m ransom, then their management want their arses kicking. Pay these extortionists their ransom only emboldens them and pays their IT costs for the next attack.
link to original post
I donít know, when itís all said and done, I suspect MGM is going to wish they could have just paid $30 mil to avoid this mess.
link to original post
$30M can buy a whole lot of IT consultants to tell them how to avoid the mess in the future. :)
of course they will all conflict with one another.
And they'll all need super user privs.Quote: 100xOdds
$30M can buy a whole lot of IT consultants to tell them how to avoid the mess in the future. :)
of course they will all conflict with one another.
link to original post
https://techcrunch.com/2023/09/14/caesars-entertainment-data-breach-cyberattack
Caesars said in an 8-K notice with federal regulators filed before markets opened on Thursday that hackers stole a copy of the companyís loyalty program database, which includes driver license numbers and Social Security numbers for a ďsignificant number of members.Ē
yike!
I'm probably one of those affected.
How to prevent the opening of credit cards and other credit lines in my name??
Quote: ams288
My company makes us do at least one yearly training class teaching us how to avoid this exact scenario.
And the security team sends out fake phishing emails occasionally to try to catch us off guard. We have to report the email as a phishing attempt. God forbid if you click the link or open the attachment - then you have to attend another special training.
My company did the same and I fell for one of them. I was very embarrassed.
Quote: 100xOddsInfo on Caesar's breach back in Aug 2023:
yike!
I'm probably one of those affected.
How to prevent the opening of credit cards and other credit lines in my name??
link to original post
In this day and age, the Microsoft stance of "Assume breach" really applies everywhere.
The fact that Caesars now announce that they were breached really shouldn't change anything for you or anyone else. For each disclosed leak like this, there are likely 5 others that have not been announced. Your data is out there. Just get used to it.
To answer the question, if you are concerned, contact each of the 3 main credit bureaus and have a freeze put on your account. It's free. And it's a minor hassle when you actually do have a valid reason for a credit check.
I didn't navigate them. But Assuming they are workable to some extent.
EDIT: No, rewards accounts are still unavailable for sign in.
Yes, the site is up, but...Quote: darkozThe websites are finally back up. They were still down an hour ago.
I didn't navigate them. But Assuming they are workable to some extent.
EDIT: No, rewards accounts are still unavailable for sign in.
link to original post
Quote:MGM Rewards accounts are currently unavailable.
MGM Rewards members may call Member Services from 6 AM to 11 PM Pacific time at 866.761.7111.
Thank you for your patience.
I guess since MGM isn't paying up they are going public.
https://twitter.com/mikko/status/1702421207738663281/photo/3
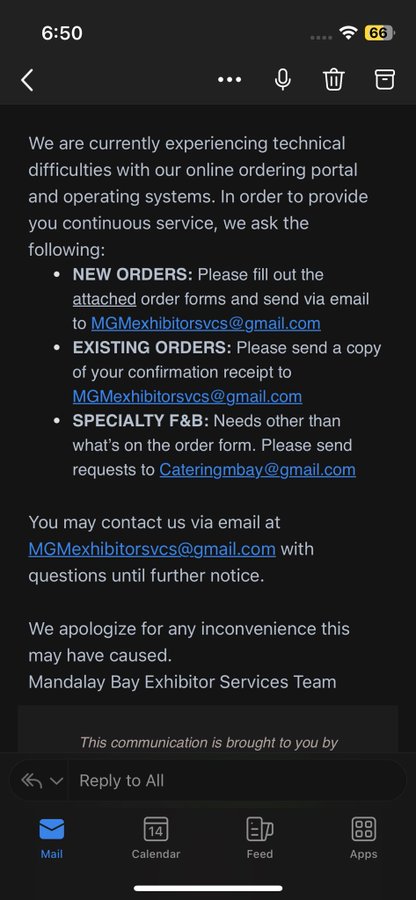
Mgm Mandalay Bay using gmail addresses to do business because of the hack.
This can't be real??
Please know we are also experiencing intermittent system issues that may impact our outlets and the ability to redeem your offers and MGM Rewardsô. When we have more information, we will share it with you as soon as possible.
(that's kind of a joke, but is kind of not a joke)
only down 7% in last 5 daysQuote: MukkeI just bought a lottery ticket some puts. It seems only appropriate to gamble in a situation like this. :)
link to original post


